IT security is a complex issue that no longer only affects large corporations. Every company has the responsibility to keep the level of information security as high as possible with the available resources. The spectrum of assets to be protected in today’s IT landscapes is very broad. From individual files to PCs and laptops, from networks to cloud services and data centers.
Comparatively few companies have the expertise to identify all the relevant areas. And equally few companies have the resources to identify appropriate measures to protect them.
The Federal Office for Information Security (BSI) has therefore developed the BSI Standards and the "IT-Grundschutz" (IT baseline protection) Compendium. These guidelines enable companies to approach the topic of information security from the bottom up and to implement it sustainably. Risks, hazards and requirements are described in detail.
What are the BSI standards?
The BSI continuously develops standards for dealing with the topic of information security. They contain recommendations on processes, various methods and procedures to achieve a high level of protection. These standards describe the procedure in IT security projects and explain suitable measures for protecting corporate IT.
Currently, the BSI standards 200-1 to 200-4 are valid. The old 100 series was replaced by the current 200 series in October 2017.
BSI Standard 200-1: Management systems for information security (ISMS)
BSI Standard 200-1 defines the requirements for an Information Security Management System (ISMS). For the establishment of an ISMS, the following are necessary:
- The definition of a safety process.
- A clear organisational structure.
- The setting and release of resources.
- A combination of different management principles.
It must be clearly defined within the company how the topic of IT security is to be approached and continuously pursued. The advantage of the standard is that it is fully compatible with ISO 27001, which means that certification according to ISO 27001 is possible after implementation of the IT baseline protection.
BSI Standard 200-2: IT baseline protection methodology
BSI Standard 200-2 describes how the requirements for an ISMS can be implemented. Whether the organisation and documentation of the security process, the creation and implementation of the security concept to the continuous improvement of information security.
BSI Standard 200-3: Risk management
BSI Standard 200-3 deals with risk management within the organisation. Here, all elementary and additional hazards are explained in detail. Furthermore, possibilities for classifying risks and how to counter them are found here. For the defence against hazards, the consolidation of the security concept is described here.
BSI Standard 200-4: Business Continuity Management
BSI Standard 200-4 provides sound guidance on emergency management within the organisation. This practical guide to setting up a BCMS (Business Continuity Management System) helps users get started with the topic. It shows numerous possibilities for implementing requirements in a timely manner.
The IT baseline protection Compendium
 The IT baseline protection Compendium offers all the building blocks to implement BSI Standards 200 – 1 to 200 – 4. Thus, a high level of information security is achieved – if applied correctly.
The IT baseline protection Compendium offers all the building blocks to implement BSI Standards 200 – 1 to 200 – 4. Thus, a high level of information security is achieved – if applied correctly.
The process modules, hazards and requirements are described in detail on more than 800 pages.
IT baseline protection – The layer model
Achieving a high level of protection according to IT baseline protection is realised by implementing different layers and building blocks. Each building block represents a specific area of the organisation in which security measures are implemented.
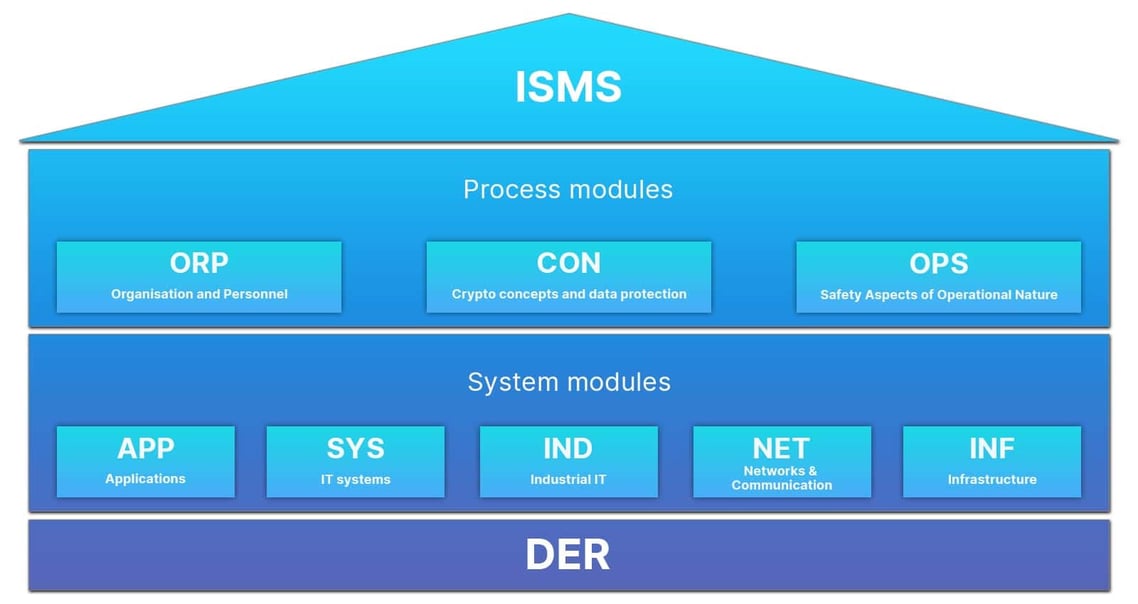
At the top of the layer model we find the ISMS. It monitors the other process and system modules through the defined organizational structure and the security process. It is therefore the basis for IT baseline protection. Below there are the process modules for ORP, CON and OPS.
- ORP: Organisation and Personnel, e.g. sensitisation and training on information security, authorisation management, and induction for new employees.
- CON: Crypto concepts and data protection, e.g. data backup concepts, deletion and destruction, software development.
- OPS: Safety Aspects of Operational Nature (Operational), e.g. patch and change management, remote maintenance and logging.
Below this are the system modules. These deal with the systems used, communication paths and infrastructures. There are a total of 5 system modules for APP, SYS, IND, NET and INF.
- APP: Applications, e.g. Office products, web servers, databases, directory services
- SYS: IT systems, e.g. Windows Server, Linux / Unix Server, Virtualisations, Clients
- IND: Industrial IT, e.g. process control and automation technology, sensors, machines
- NET: Networks and Communication, e.g. routers and switches, firewalls, WLAN and LAN management
- INF: Infrastructure, e.g. buildings, data centres and server rooms, home office / workplaces.
The last building block is Detection and Response (DER). Since this can extend to all other building blocks, as both systems and processes can be monitored, it independently forms the last level.
This module is responsible, for example, for the detection of security-relevant events, audits and revisions as well as the handling of security incidents.
Elementary threats
The IT baseline protection Compendium devotes an entire chapter to the elementary threats that pose a risk to people, systems and the organization itself. The detailed breakdown of threats and their possible causes gives users a more comprehensive understanding.
The list of threats starts with “simple” incidents that negatively impact the availability of systems (e.g., fire or water damage). More complex threats (e.g., electromagnetic interference) are also covered. Finally, the IT baseline protection Compendium also mentions non-technical threats, which primarily take human factors into account. This starts with a loss of personnel and extends to incidents of coercion or corruption.
The i-doit pro Add-on VIVA2
With the i-doit pro Add-on VIVA2, companies and organisations can implement and document IT baseline protection directly in i-doit. The risk assessment can be carried out for any assets and suitable measures can be linked from the catalogues.
This makes it possible to set up an ISMS according to BSI standards 200-1 and 200-2, which is seamlessly integrated into the CMDB. All building blocks of the IT baseline protection compendium can be linked to assets from the CMDB and their implementation can be controlled. The degree of implementation of the measures can be monitored at any time through the predefined reports. The documentation of the need for protection can also be displayed visually.
For users of the ViVA1 add-on, the VIVA2 add-on has a tool for migrating existing data.
Import of the entire IT baseline protection compendium
The IT baseline protection Compendium consists of numerous threats, requirements and measures to avert danger. This means it already contains all the information needed to achieve a high level of security. The entire IT baseline protection Compendium is available for you to download from the customer portal. You can import it into the CMDB with just one click to access all requirements and threats and assign them to your assets.
 The IT baseline protection Compendium is available for download in the customer portal.
The IT baseline protection Compendium is available for download in the customer portal.
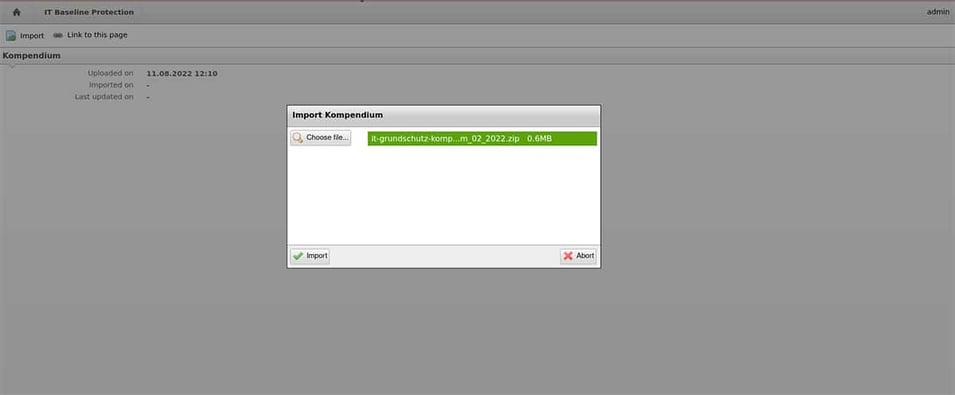 The IT baseline protection compendium can be imported directly into ViVA2 to gain access to all hazards and requirements.
The IT baseline protection compendium can be imported directly into ViVA2 to gain access to all hazards and requirements.
Selection of the process modules
Depending on which asset is being considered, various process modules from the IT baseline protection compendium can be added. From applications (APP) to systems (SYS) to infrastructure (INF) and detection (DER), all process building blocks can be selected.
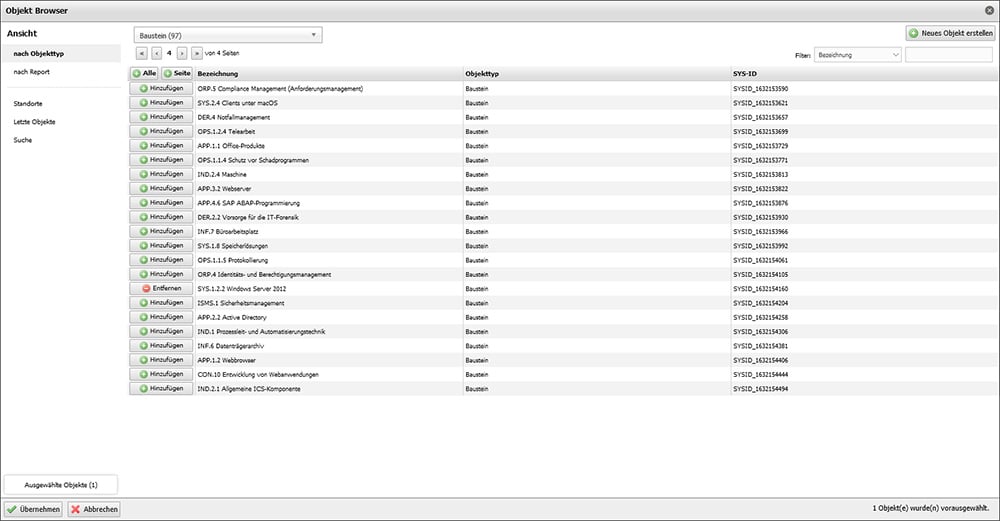
After selecting a module, the associated basic, standard and requirements with increased protection needs are automatically loaded in the category “IT baseline protection check”. Based on this overview, the implementation of the requirements can now be planned and controlled.
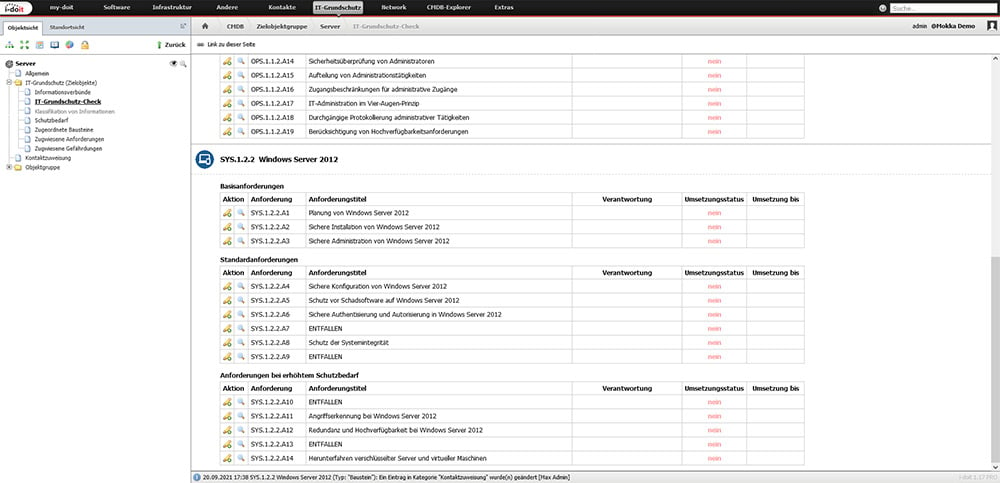 All requirements of the selected building blocks are loaded automatically.
All requirements of the selected building blocks are loaded automatically.
By processing the requirements, work steps can now be defined and delegated to responsible persons. In addition, the one-off and recurring efforts can be recorded.
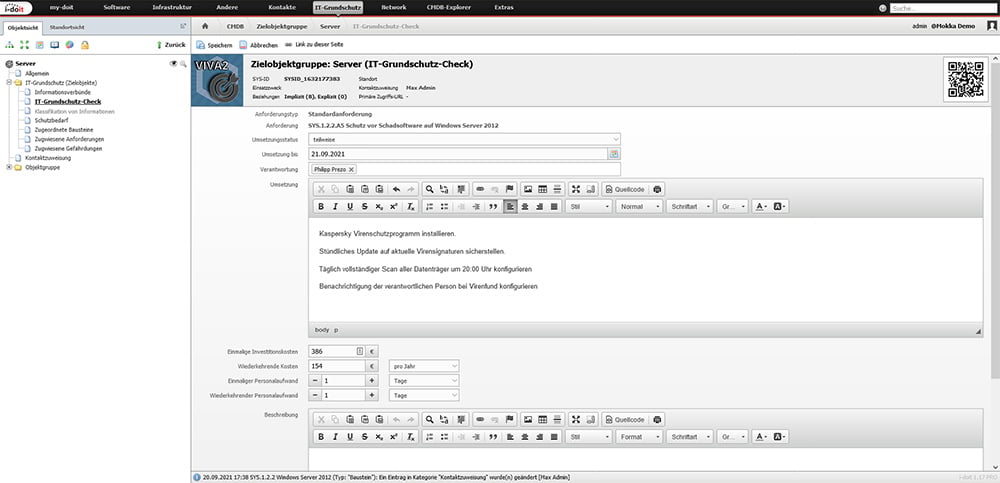 The implementation of the measures can be specified directly in the requirements of the building blocks.
The implementation of the measures can be specified directly in the requirements of the building blocks.
Detect threats automatically
Adding the building blocks also automatically links the threats that have been defined by the BSI. This allows responsible persons and technical staff to determine exactly in which area you should take additional measures to achieve a higher level of protection.
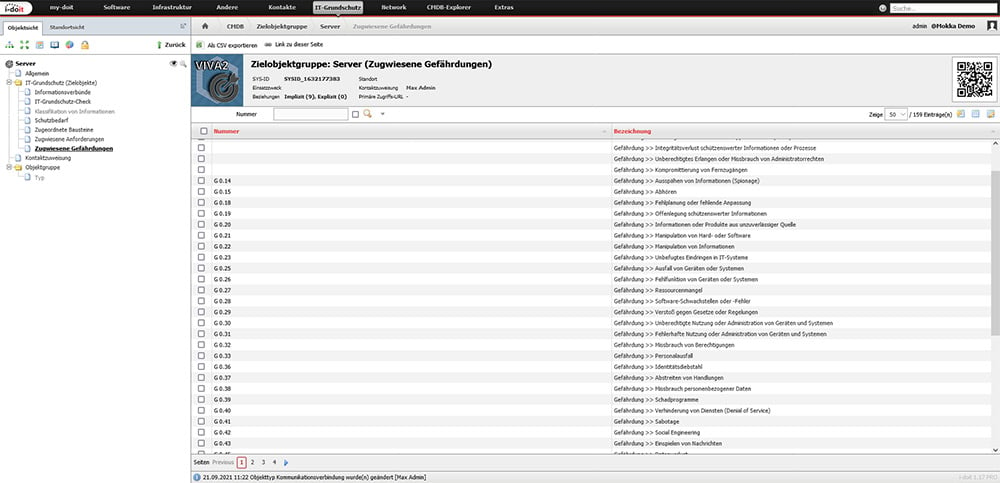
In addition to the defined threats of the IT baseline protection Compendium, the VIVA2 add-on also provides you with numerous additional threats with practical knowledge. In total, the VIVA2 add-on contains almost 600 threats that can be assigned to assets for risk analysis.
Evaluation and continuous improvement
The data entered can be evaluated in various predefined reports. For example, each employee can list an overview of the requirements assigned to him or her in order to always have them in view. Applications that have not yet been installed or hardware that has not yet been assigned to a location can also be easily evaluated via the respective reports. In this way, specialists and managers can monitor the progress of the project at any time.
 With the reports provided, you can always keep an eye on the progress of the implementation.
With the reports provided, you can always keep an eye on the progress of the implementation.
Through regular evaluations, the progress of implementations can be constantly monitored. This also allows additional necessary measures to be identified in order to further increase the level of protection. In this way, you can achieve a continuous improvement of your information security standard.
The advantages of the i-doit VIVA2 add-on
The VIVA2 add-on is the perfect complement for companies aiming for an overall higher level of protection or ISO 27001 certification according to IT baseline protection. Through seamless integration into the i-doit CMDB, all assets can be viewed and linked to the building blocks from the IT baseline protection compendium.
- Structured development of an information security standard
- Information basis for one-off and recurring expenses
- Continuous improvement (CIP) of information security
- Reducing risks and their probability of occurrence
- Automatically detect risks and threats
- Better understanding of IT, professional and managerial staff
- Improving the availability of systems and services
- Prevent cyber attacks
- Certified standard means competitive advantage
- Central evaluation of the information security standard
Through the automatic allocation of basic and standard requirements as well as requirements for increased protection needs, threats can be identified and measures planned and controlled. The native integration also provides you with core functions of the CMDB such as the granular rights system, templates, reporting, API and many other convenient functions for data maintenance and evaluation.
The VIVA2 add-on is particularly suitable for companies:
- who would like to carry out an analysis of availability, integrity, confidentiality and authenticity (VIVA) of the IT network and the processes according to IT baseline protection 200-X.
- who plan the development of an ISMS.
- who aim for certification according to BSI IT baseline protection or ISO27001


 The IT baseline protection
The IT baseline protection