The i-doit CMDB offers extensive functions for documenting and managing assets. The modelling of services and the representation of dependencies and relationships is included in the scope of functions right from the start. Thus, i-doit has all the functionalities needed to implement IT Service Management. However, unlike all-in-one solutions, the system does not offer discovery and monitoring. And there are good reasons for this.
All-in-One solutions
If you have an overall solution that already includes all the components for IT Service Management, it’s very convenient. Discovery for finding assets, Monitoring for querying the live status of systems, and a Service Desk for internal and external communication. This sounds good at first, but it also entails a whole host of drawbacks.
For one thing, you make yourself very strongly dependent on the manufacturer. The individual systems such as Discovery, Monitoring & Service Desk are developed by a single manufacturer. Due to the lack of specialisation, these usually have a much more limited range of functions compared to stand-alone solutions. If your company places new requirements on the solution, it’s difficult for the manufacturer to implement with the existing personnel resources. If the solution ultimately no longer meets your requirements, you are forced to replace it completely. A mammoth project that requires a lot of time and resources. The whole situation is different with a modular ITSM suite.
Characteristics of an ITSM Suite
- All functionalities are integrated in one tool
- High dependence on one manufacturer
- Functions mostly limited
- With new requirements, expansion is difficult
- Complete system must be replaced
Advantages
- All tools for IT Service Management integrated in one solution
- Support directly from one vendor for all requests
Disadvantages
- High dependence on a single manufacturer
- Functions mostly limited/less in depth
- New requirements and expansion is difficult
- Complete system must be replaced
Modular ITSM-Suite
A modular ITSM suite is made up of various solutions. The basis is a CMDB such as i-doit, in which all information flows together. Tools such as Discovery, Monitoring and Service Desk are selected and connected according to the company’s specific requirements. This approach offers a real added value. The individual solutions are fully aligned to the respective discipline. Each solution focuses on just one discipline and thus offers significantly more functions than is the case with all-in-one solutions. In many cases, the cost of the tools used is also significantly lower because they have been designed for a broader target group and have undergone constant further development. If one of the solutions used no longer meets the requirements, it is simply replaced by another. It is not usually necessary to migrate all the data and information.
Advantages
- Can be adapted quickly to new requirements
- Inexpensive modular design
- Fully aligned to the respective discipline
- New requirements can be implemented quickly
- Modules can be exchanged at any time
Disadvantages
- May be more complex in initial configuration due to the larger feature set.
- Support from different manufacturers may be necessary
JDisc and i-doit
JDisc and i-doit work hand in hand as a modular ITSM suite. JDisc is responsible for regular discovery and finding of assets in the network. It scans the entire network for devices such as servers, clients and peripherals. Cabling, virtualisation and hosts are also recorded as well as software and licences. JDisc regularly transfers this information to the CMDB i-doit. Here this information can be expanded, linked and modelled into services. A fully automated system network that relieves your employees and makes information usable centrally.
IT-Services with i-doit
IT services are usually complex. Different components are required for functionality and availability. These can be systems, software, services, people, contracts or other services on which there is a dependency. An “email service”, for example, does not only consist of the Exchange software for smooth operation. It also requires a physical server, a licence and a gateway to the Internet. Not to mention the contract with the ISP and services such as DNS. If any of these components are compromised, the “email” service will also be compromised.
Modelling IT services makes the usual jungle of IT services more transparent. Changes to the IT infrastructure can be planned much more easily because the dependencies are clearly identifiable on the basis of the modelled services. The costs for services and their components can also be calculated and, if necessary, replaced by more cost-effective alternatives.
Modelling services bring companies a whole range of benefits:
- Better understanding between employees and the IT department
- Identify and optimise service costs
- Audit services and their performance
- Model device and service failure
- Automatically check consistency of services
Model email service with data from Discovery
i-doit has a preconfigured object type for modelling services. To create a new service now, simply open the already pre-defined object type “Services” and create a new object.
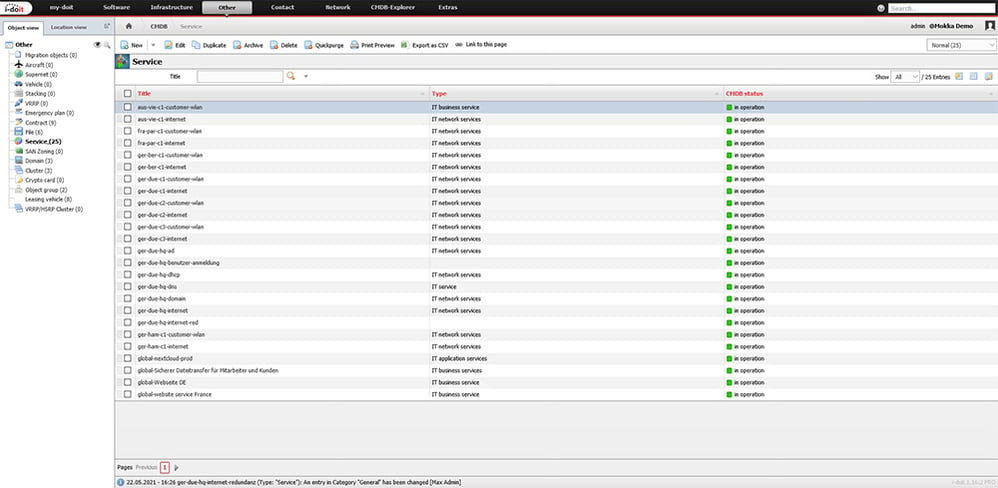
After assigning a name for the service you want to create, such as “Email”, the respective components are added in the “Service” folder.
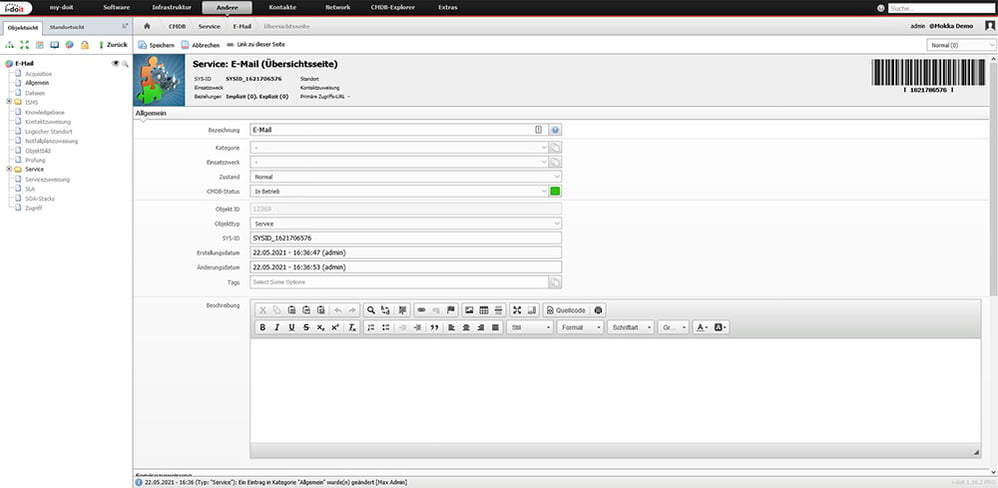 Services can be created as objects in i-doit just like any other assets.
Services can be created as objects in i-doit just like any other assets.
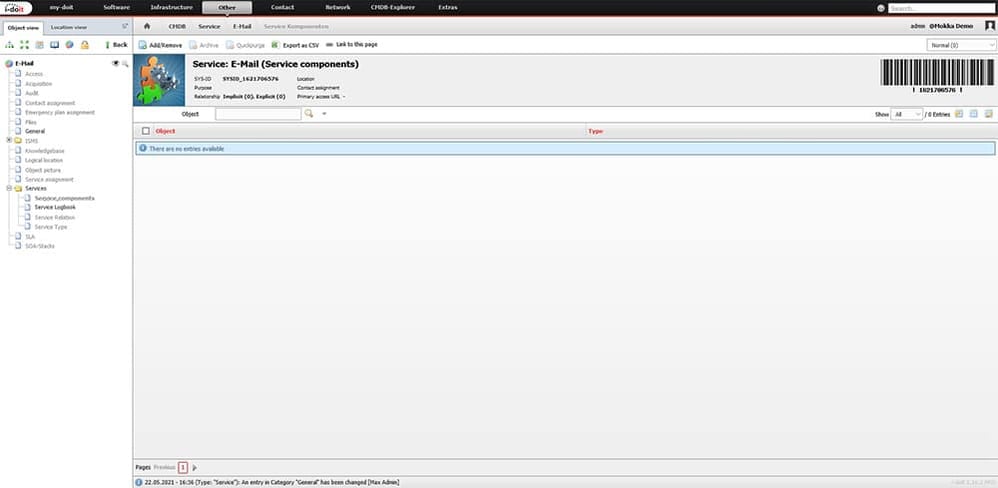 After creation, various components can be added to the service.
After creation, various components can be added to the service.
Any asset created in i-doit can now be added to the service as a component. Whether contracts, licences, people, systems, services or other services. Everything that is necessary for the functionality and availability of the service.
To manually create all the required assets for modelling services is time-consuming, depending on the state of the documentation. Therefore we use the Discovery Tool JDisc to capture the infrastructure and import it into i-doit.
Discovery with JDISC
JDisc scans networks or subnets for systems and devices. From simple clients, servers and hosts to wireless access points, VoIP phones and peripherals, it detects almost any device. The device only needs to be connected to the network or to a device on the network. JDisc collects information about all devices by using various protocols such as WMI or SMNP.
Additionally, it can log on to systems with stored credentials to retrieve information directly from the systems. In this way, it is able to recognise even complex services such as Active Directory and capture the information contained therein. Also the installed software, the used licences and licence keys as well as used system services are read out.
Even occupied and free ports, cabling and interfaces are detected with all the performance characteristics. JDisc is a comprehensive discovery tool that when it comes to network discovery, leaves nothing to be desired.
JDisc system requirements
JDISC can be installed and operated on using any 64-bit Windows operating system. It requires very few resources. The actual consumption depends on the size of the network to be scanned. For a network with 1000 – 10,000 devices, a processor with at least 2 GHz, 8 GB RAM and 8 GB free hard disk space are specified by the manufacturer.
Start Discovery and import
The i-doit CMDB offers a free integrated interface for the Discovery Tool JDisc . Via this, discovered systems from JDisc are imported directly into the CMDB.
If current data is needed in the documentation, the discovery can be started via the web interface. JDisc communicates with i-doit via the API.
Discovery jobs can be started via the admin area to transfer the newly discovered information into the i-doit CMDB. A call of the JDISC application on the server is thus no longer necessary.
Discovery Server in different locations
Discovery is often required in different locations. These can be different locations, branch offices, an external data centre or the cloud. The problem: not all locations are networked with each other.
A secure VPN connection would place an additional load on the network. You can get around this by installing and configuring another JDisc instance in the location. This instance only scans the networks at the site. It then sends the results to the central i-doit instance. There, the data is merged. This way, even complex networks can be captured and summarised in a central CMDB.
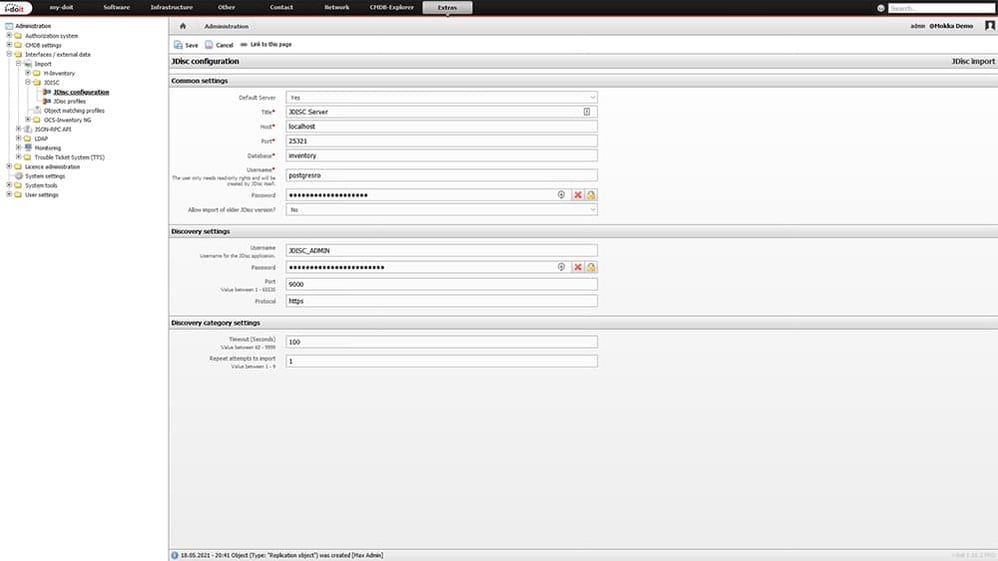
The respective JDisc server instances can be added in i-doit and used individually for importing data.
Control import of systems and information
For the import of systems and information, different profiles are created as required. On delivery you will find the following pre-configured profiles:
- Complete Import: VComplete import of all systems and information from JDISC into i-doit.
- Network: All devices relevant for the network infrastructure like routers, switches and patch panels.
- Server and Clients: Complete import of clients (thin clients, PDAs, desktops, notebooks) servers.
- Others: Full import of other devices like access points, Hyper-V instances, IP phones etc.
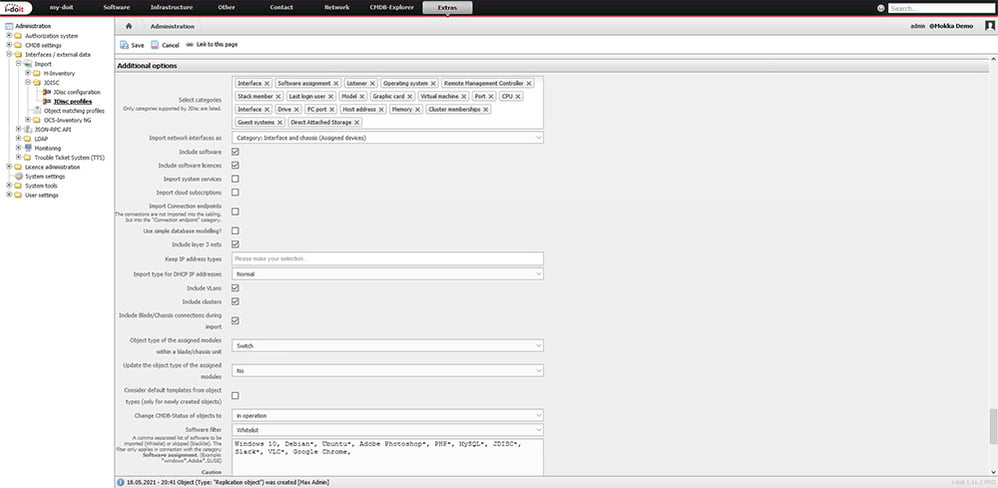
The device classes to be imported are configured via these profiles. Likewise, the information to be imported from these devices is defined here. This makes it possible to ensure a very granular import of data. By using different profiles, how up-to-date the data in the CMDB is can be perfectly controlled.
Selectively import or discard data
To make sense of the data received from JDisc, a selective import is recommended. JDisc detects every system service, every installed software and every application. That’s why the imported amount of data quickly becomes very large. Another problem: You fill your CMDB with information that you might not need at all. i-doit allows you to include and exclude information for import. This way you define exactly which data will be taken from JDisc and which will be excluded during the import.
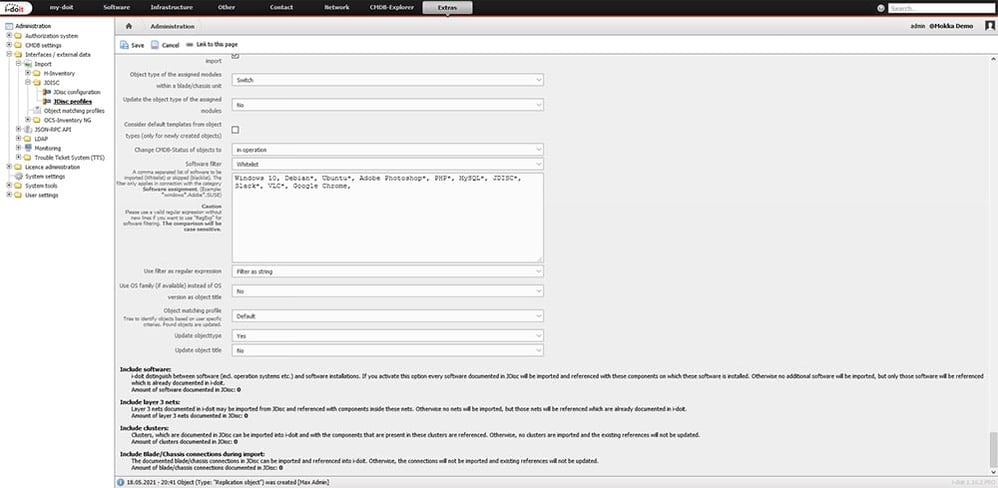
JDISC: Import of information
To start the import of assets, go to Tools -> CMDB -> Import. There you select the JDisc Import Module in the left navigation. Here we now select one of our previously configured JDisc servers.
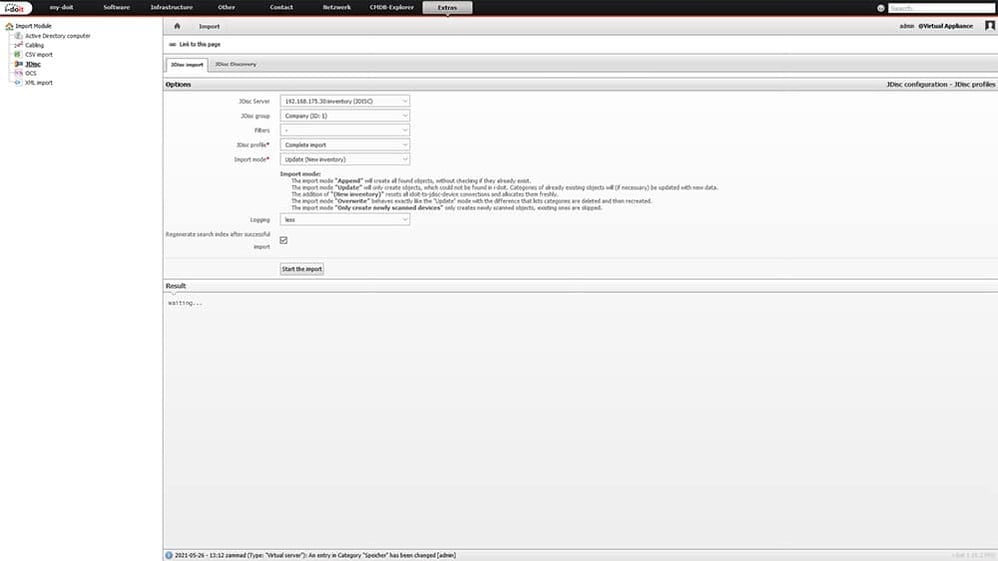
Via the button “Start import process” a connection to the JDisc server will now be established. Afterwards the existing information will be compared with the data in the CMDB. Depending on the selected profile and mapping settings, new objects will be created, existing objects will be overwritten with information or completed.
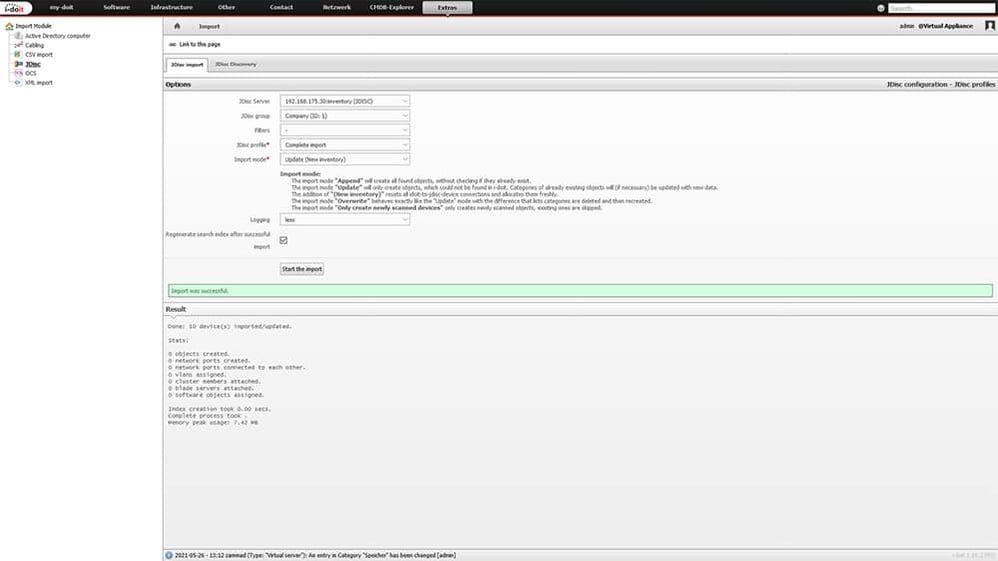
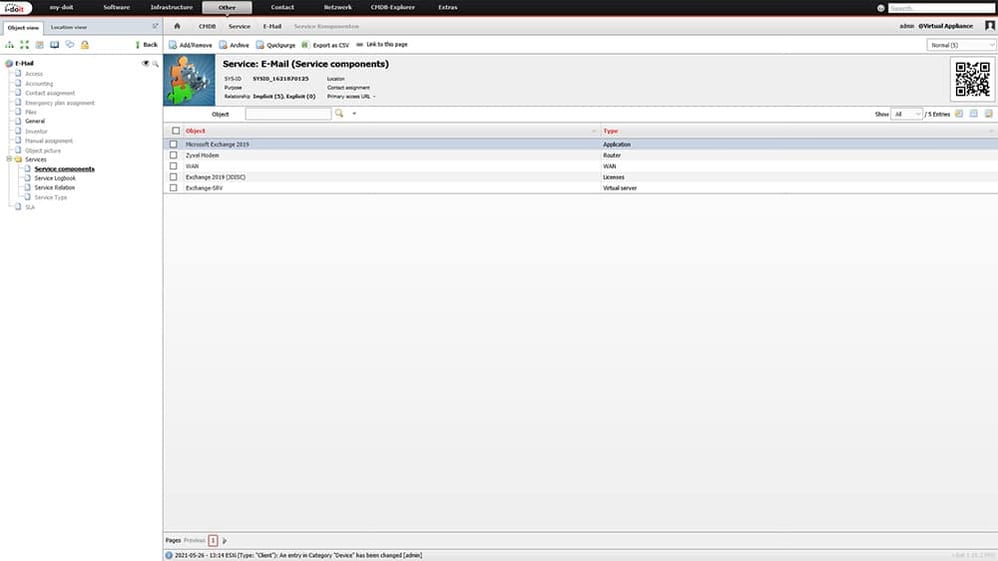
The assets that have now been imported can be used for modelling the services. To do this, we switch back to the created service object “Email” and add the necessary components. Our service “Email” consists of:
- the virtual machine
- the Exchange software
- eExchange licence
- the WAN line
- the modem
We can now open the service via the CMDB Explorer. There we check the dependencies and relationships between the assets. Not only the selected service components are displayed, but also the assets required for them, such as the physical EXSi server on which the Exchange virtual machine is run.
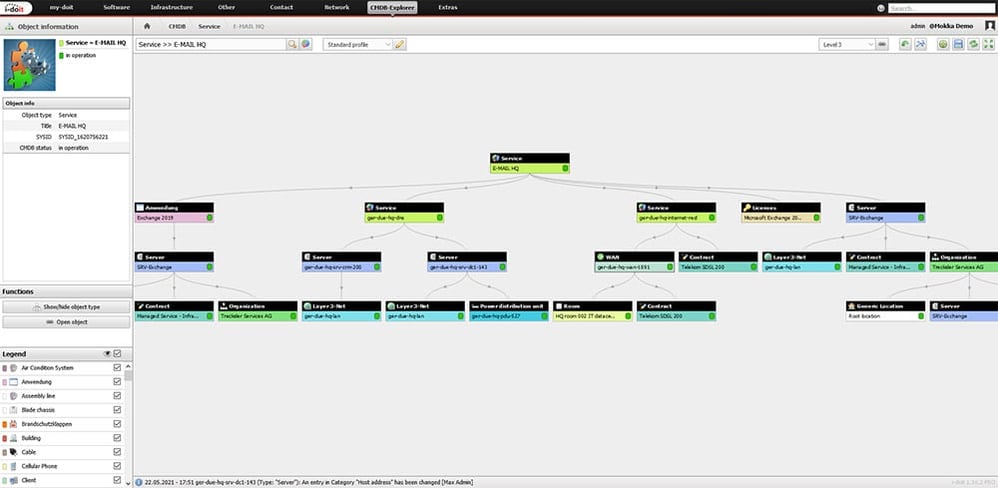
If this now changes to the “faulty” state, we can see from the service view why the service email is currently faulty. If a fault is now reported, the responsible HelpDesk employee can call up the entire service in the CMDB Explorer. There they check whether one of the components is disrupted and if so, which one. This makes it easy to check the consistency of services.
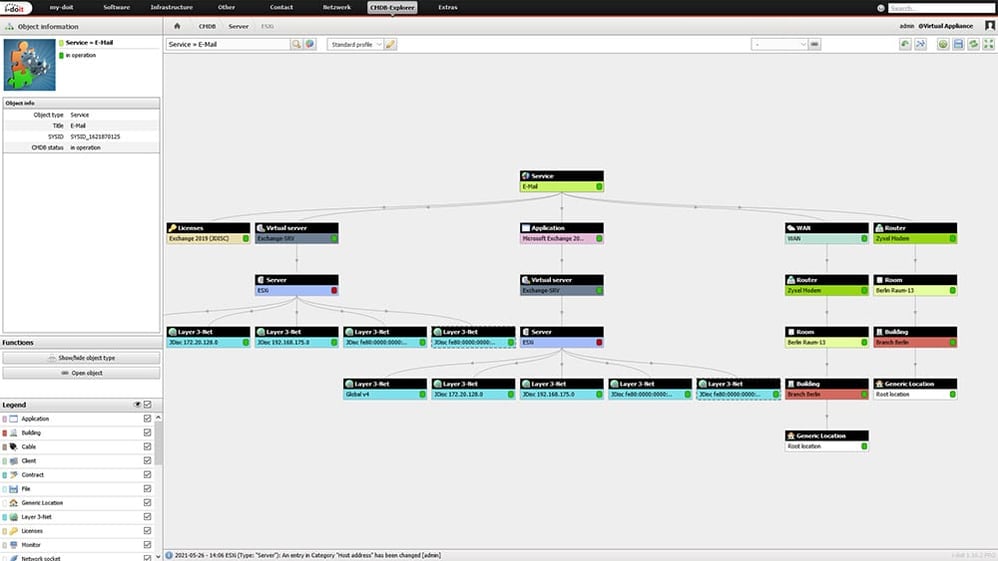 By calling the service in the CMDB Explorer, all components and their status can be checked.
By calling the service in the CMDB Explorer, all components and their status can be checked.
Modelling Services with JDisc and i-doit
As you can see, modelling services with i-doit is quick and easy. With JDisc you identify assets in your network and import this information regularly into the CMDB. This not only reduces the documentation effort, but also provides you with up-to-date information and the ability to link it to other assets.
The combination of JDisc and i-doit is a field-proven solution for implementing IT Service Management. If you would like to know more about this topic, we look forward to you getting in touch.