
Ready for ISO 27001
Prepare for certification with confidence.
With i-doit and its available add-ons, you get a complete ISMS suite for the highest demands that can be variably adapted to new requirements.
ISO 27001 certfication with i-doit
Successful certification to ISO 27001 requires not only an information security management system but also the recording of assets and the creation of the necessary documentation, documents, security policies and guidelines.
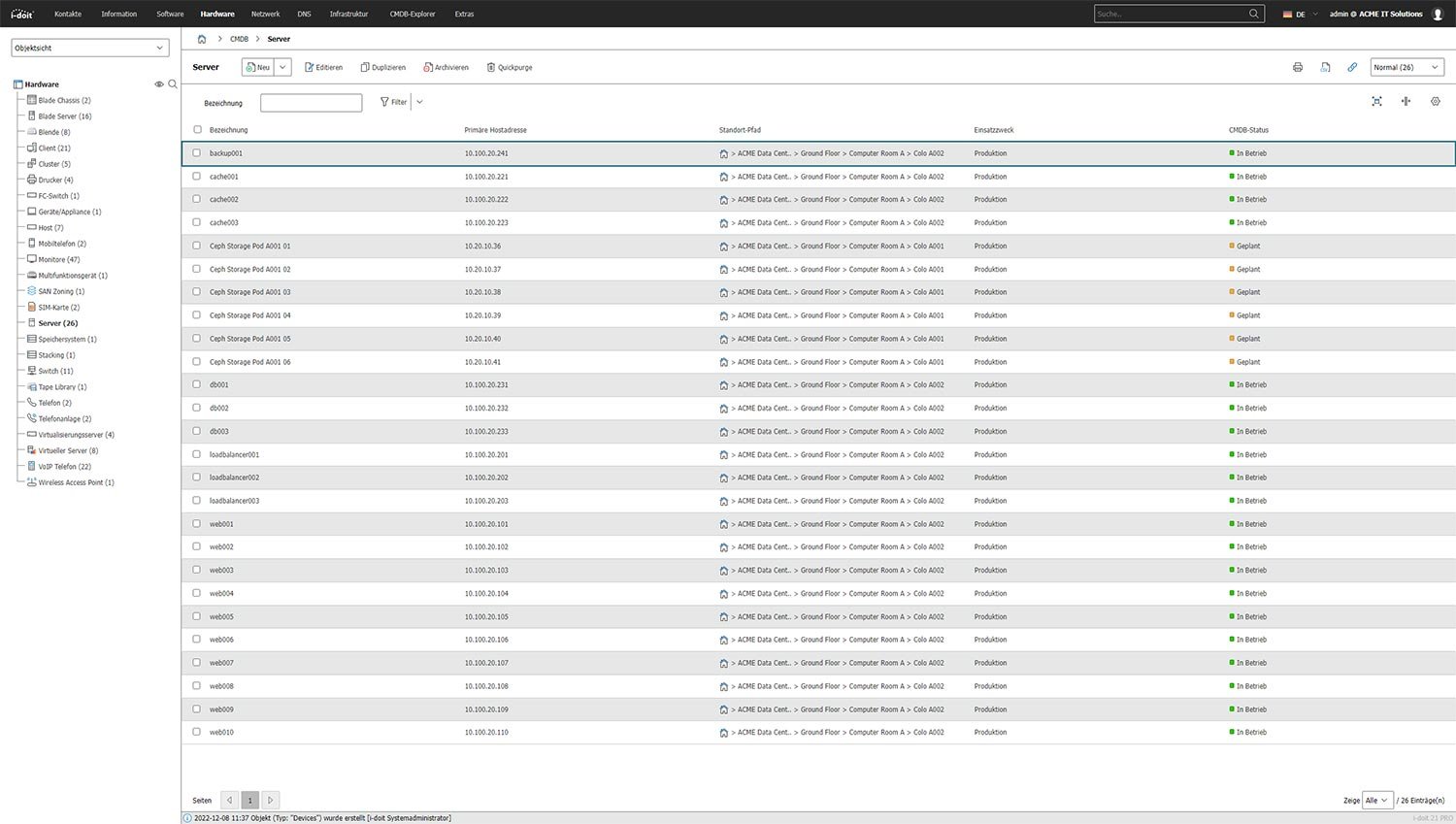
Documentation of Assets
With over 100 predefined object types, you record every asset in your organization in i-doit. If you need new types of classes, you can configure and roll them out in just a few minutes via the web interface.
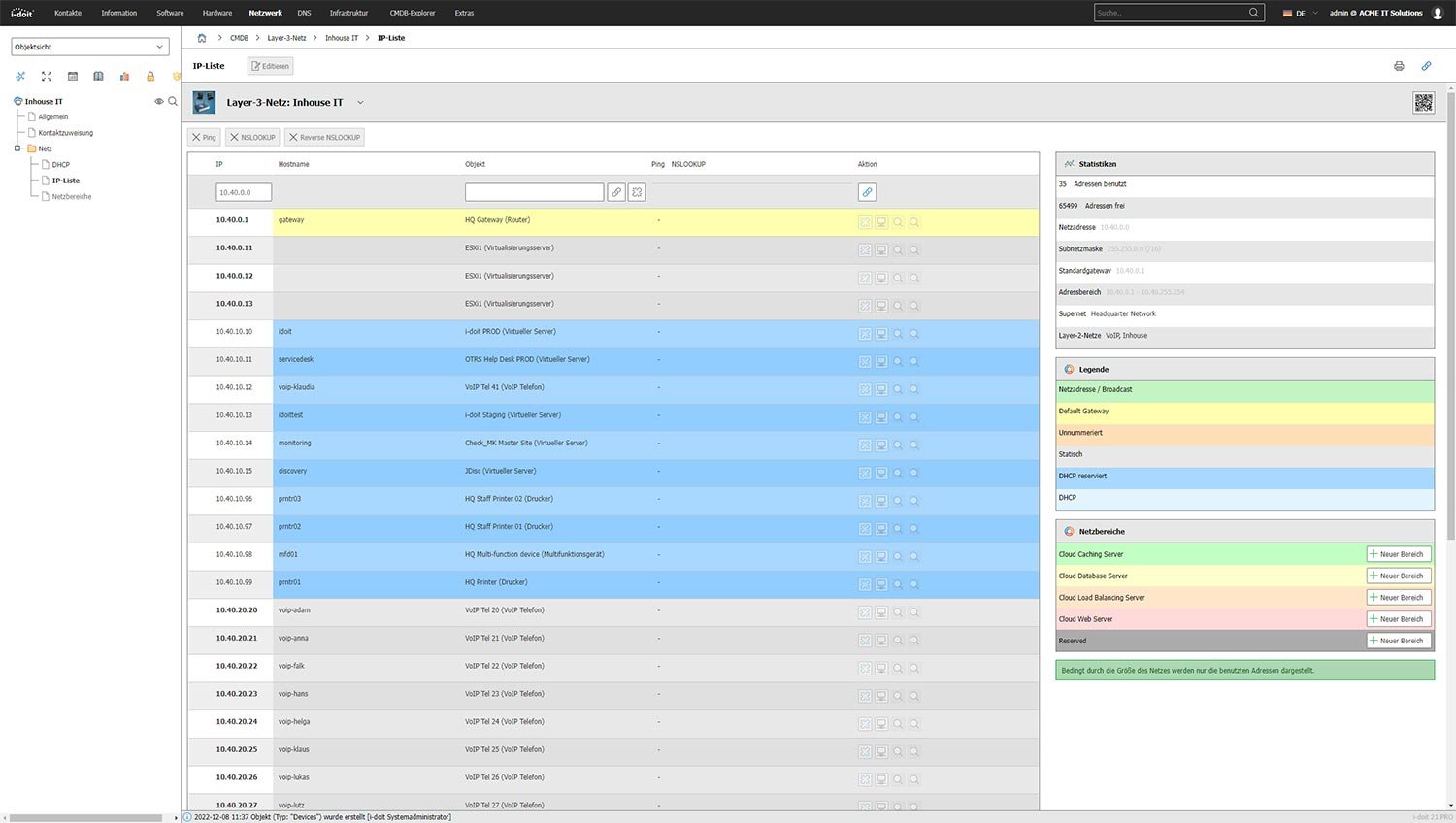
Systems, networks and data centers
The foundation of any ISO 27001 certification is the recording of systems, networks and data centers. In addition, i-doit has IP address management (IPAM), which significantly simplifies the planning of new components and management of existing networks.
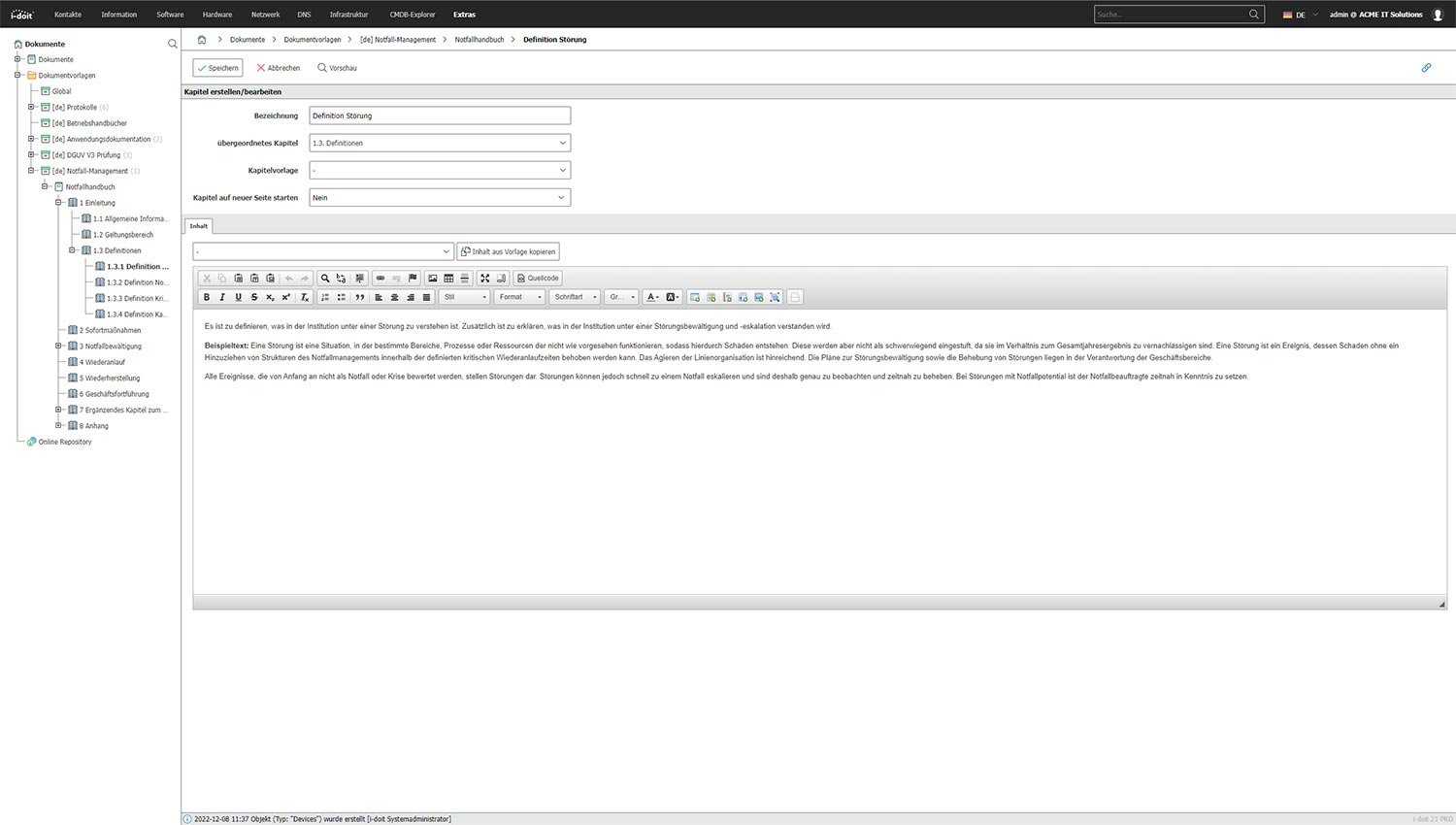
Asset- and system manuals
You gather all the captured information into concepts and system manuals with just a few clicks. You simply export the automatically created documents in PDF format. This way, you always have a copy of your most important documents at hand.

An ISMS can be that simple
Ready for ISO27001 certification with i-doit pro
We guide you LIVE through the i-doit ISMS. In a detailed LIVE demo, our experts will guide you through the system and show you how you can protect your investments with i-doit ISMS.
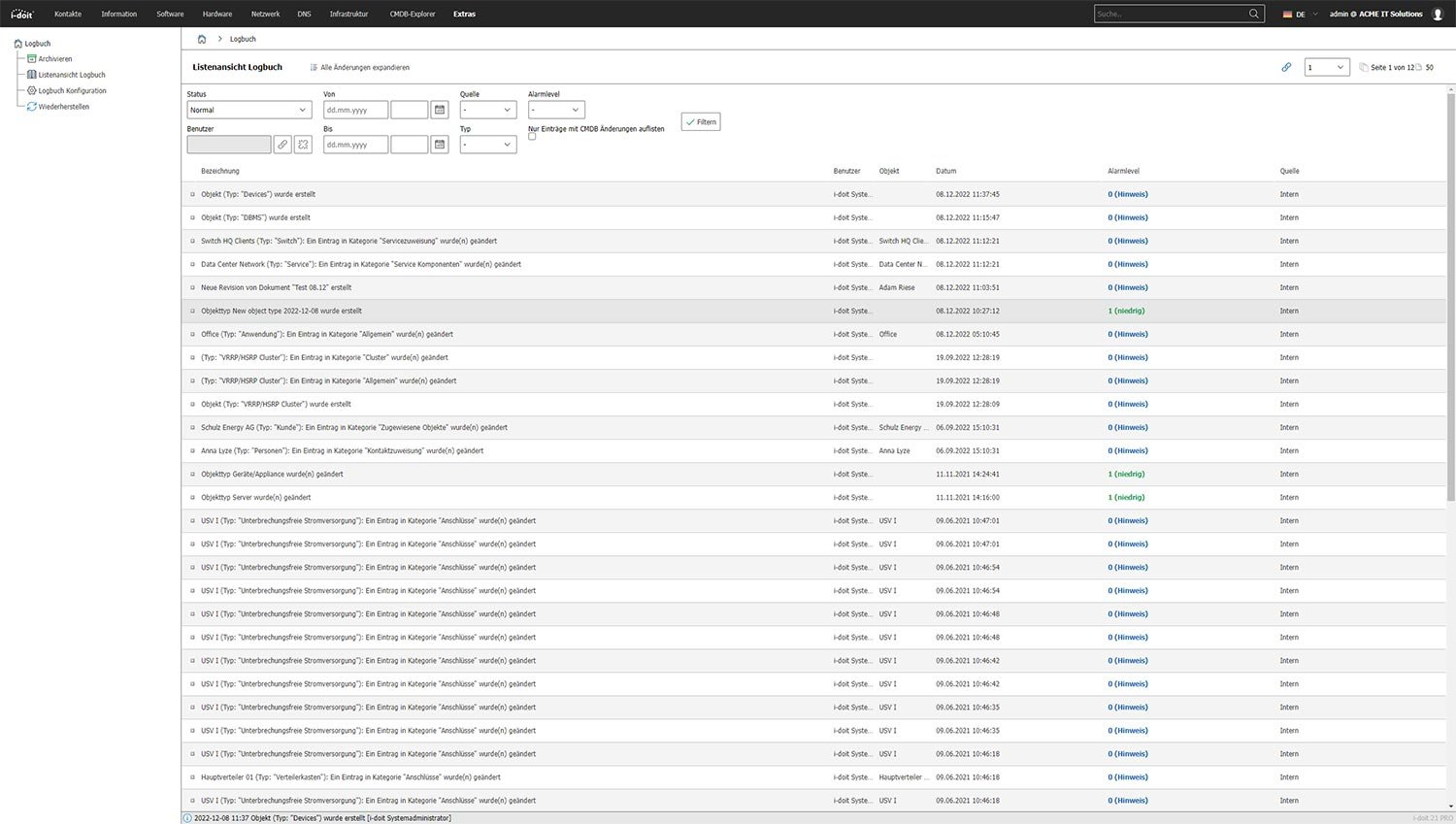
Traceability of changes
All changes to existing or newly created assets are recorded in the logbook. By recording the status of each asset and automatically documenting changes, you have complete change and configuration management.
Emergency and safety concepts, documents and guidelines
You create security concepts individually for each scope. You link the associated documents and policies directly to the respective locations, devices, and other assets. Restrict access to these documents to individuals and groups of individuals as needed.
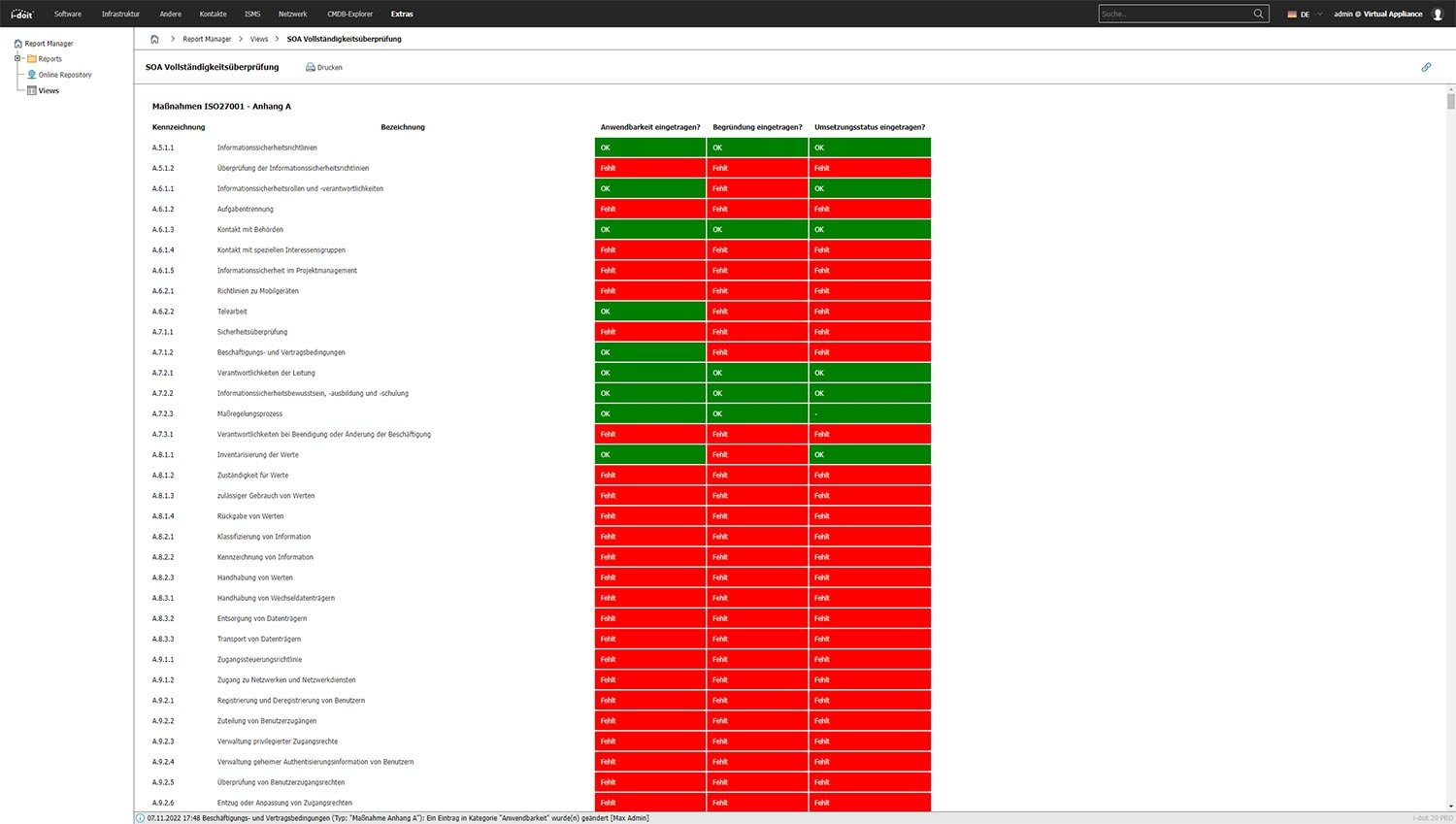
Risk und Gap Analysis
Perform the risk analysis and review for each recorded asset directly in the CMDB. Based on the review, you can assign risks from the ISO27001 catalog of measures or the IT-Grundschutz compendium. Use the gap analysis functionality to identify and close gaps in risk management.
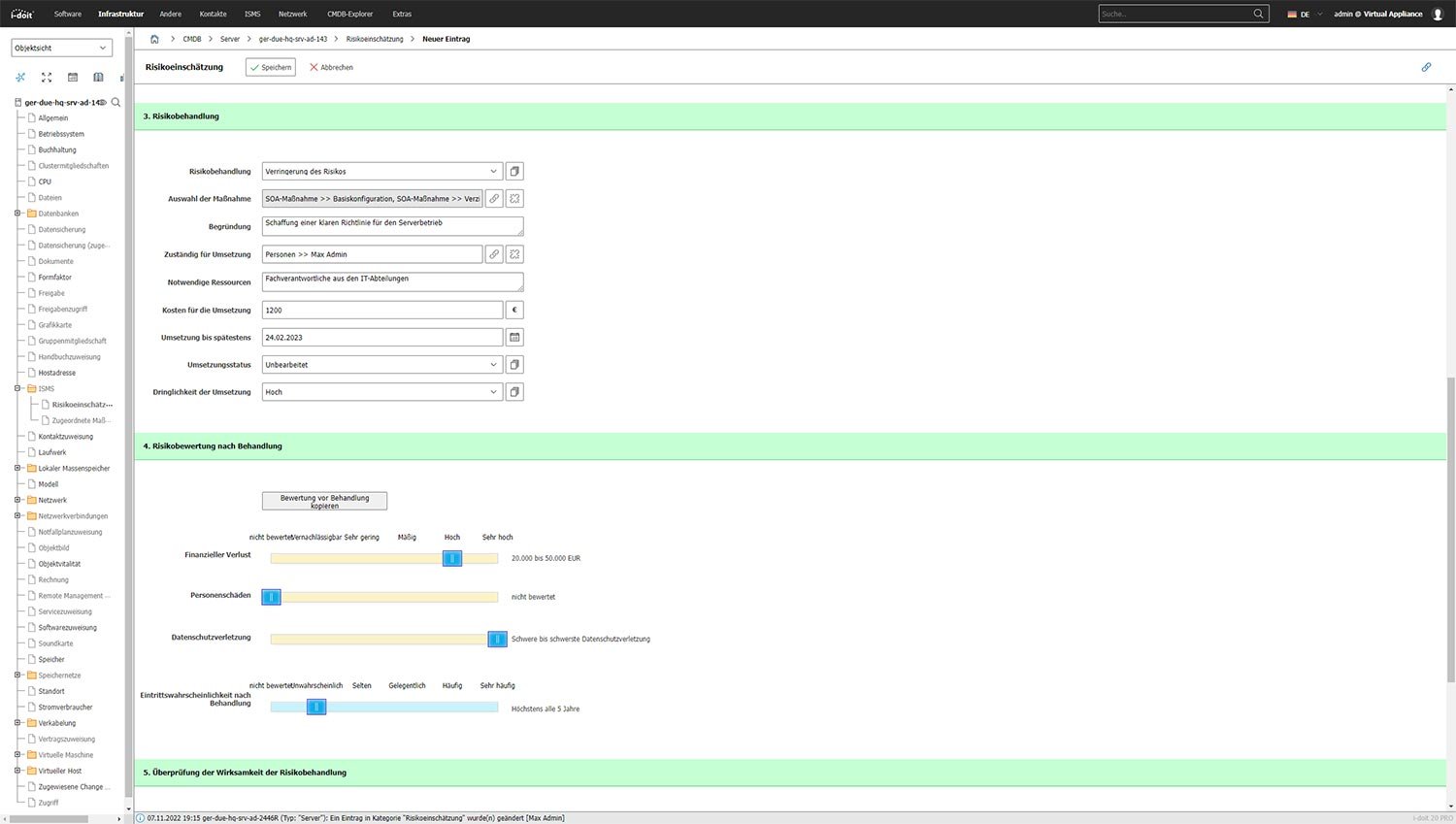
Task Management
You simply assign planned measures to a responsible person. You record the necessary resources and their costs individually for each measure. The prioritization of tasks is part of the standard procedure, as is the classification of the implementation status and the definition of deadlines.
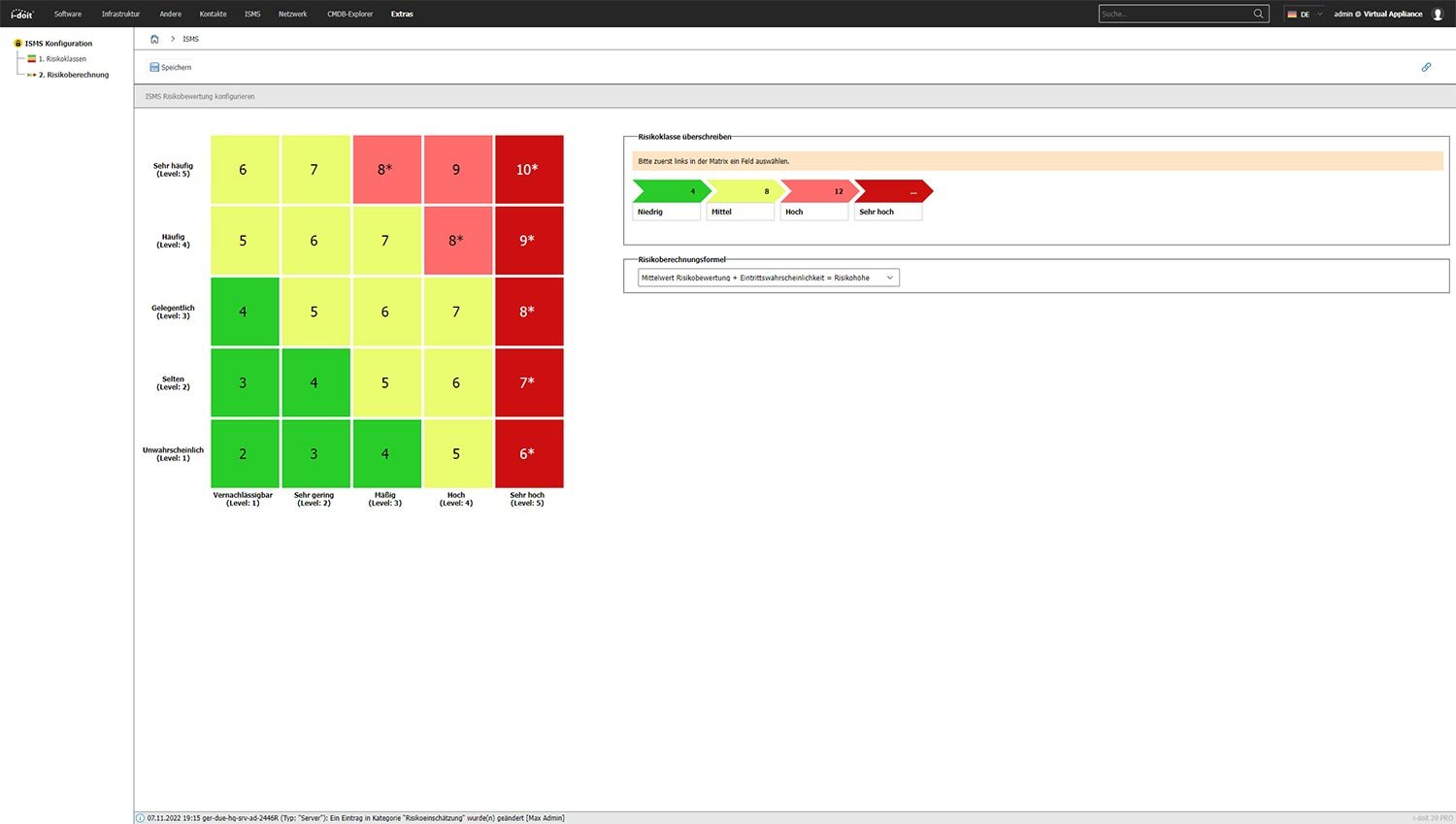
Risk calculation
For the classification of risks and their calculation, specify the formula to be used. This will be used in the calculation and creation of the risk matrix and applies to all risks considered. Specify different criteria individually, e.g. financial loss or impairment of task performance.
Request your free LIVE demo now
We guide you LIVE through the i-doit ISMS
In a detailed LIVE demo, our experts will guide you through the system and show you how to protect your investments with i-doit ISMS.

.png?width=708&height=350&name=i-doit_Logo_(ohne_claim).png)
